Follina [CVE-2022-30190] OR MalDoc simulation plan | 01 June 2022
As per Microsoft's assessment, CVE-2022-30190 is categorized as a remote code execution vulnerability. This vulnerability emerges when MSDT is invoked through the URL protocol by a calling application, like MS Word. An attacker who effectively exploits this vulnerability gains the ability to execute arbitrary code, utilizing the privileges of the calling application. This could permit the attacker to install applications, access, modify, or delete data, and even establish new user accounts within the scope of the user's permissions.
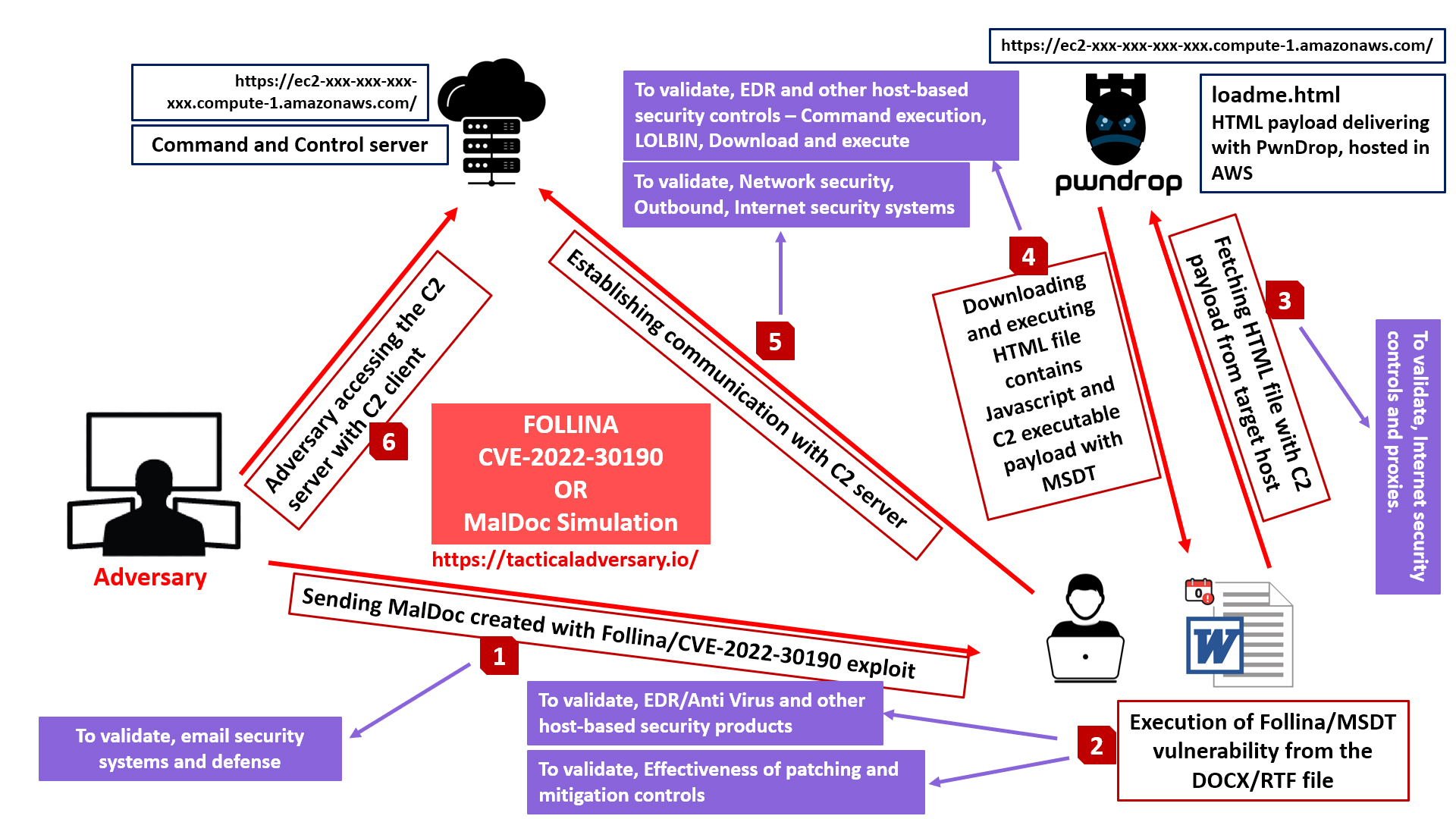
This simulation plan has been created to assess how your organization would respond to a full attack chain which would leverage Follina or MalDoc exploits. Step by step actions will be updated on this blog post.
1. Sending MalDoc created with Follina aka CVE-2022-30190 exploit.
This involves crafting and sending a MalDoc created with the Follina exploit. The goal is to test the organization's email security controls, such as spam filters, malware sandboxes, and phishing detection and qurantine tools.
To validate, email security systems and defenses
This activity would validate the email security controls and security products. Email gateways should detect and quarantine the MalDoc. Sandboxing solutions should analyze the behavior of the attached document and flag it as malicious or at least as suspicious. Effective email defense systems reduce the percentage of end users receiving and malicious files in their inbox.
2. Execution of Follina/MSDT vulnerability from the DOCX/RTF file..
Once the downloaded document is opened, it triggers the Follina vulnerability, allowing the execution of arbitrary code. This activity could validate the capabilities of endpoint detection and response (EDR) systems, anti-virus software, and other host-based defenses.
To validate, EDR/Anti-Virus and other host-based security products
The EDR or anti-virus products must detect the unusual behavior, such as the invocation of msdt.exe or the suspicious arbitrary code execution. If the existing security products were not able to detect it, well there are some huge gaps in the deployed products.
To validate, Effectiveness of patching and mitigation controls
This activity can also help to validate the patching and mitigation controls, ensuring that the system has been updated to mitigate CVE-2022-30190 or other workarounds are enabled.
3. Fetching HTML file with C2 payload from target host.
After the execution the malicious document try to fetch an externally hosted HTML file containing the payload for C2 communication.
To validate, Internet security controls and proxies
This activity helps to validate the internet security systems, such as web proxies and URL filtering tools. Outbound requests to known malicious domains must be blocked by the respective products and alerts must be triggered. If thats not the case, there are some work to do with your outboud security controls.
4. Downloading and executing HTML file contains Javascript and C2 executable payload with MSDT.
The HTML payload file downloaded in the previous step contains embedded JavaScript and a C2 executable payload, which was downloaded and executed. This "Download and Execute" stage validates the organization's capability to detect and block such common attacks vector.
To validate, EDR and host-based security controls - Command Execution, LOLBIN, Downlaod and Execute.
This activity helps us to evaluate the endpoint secuirty controls. In an ideal scenario, EDR products must have detected the use of Living Off the Land Binaries (LOLBins) to execute commands. Also the execution of C2 agents or payloads. If the validation uncovers the inefficacy of security products such as EDR, AV, then it is time to fine-tune your security products.
5. Establishing communication with Command and Control (C2) server.
This is where the payload would establish communication with a C2 server to receive commands to carry out further attacks. This would again assess the outbound traffic filtering security controls deployed in the organization. This is an important activity to emulate because, as attackers, we always come up with creative ways to bypass the outbound traffic filters to get our reverse connection back.
To validate, Network security, Outbound connections, Internet security systems.
This activity would help us validate outbound connection management, internet security systems, outbound firewalls, IDS, etc. These systems are expected to identify and block unauthorized connections to external servers. Monitoring systems must detect and flag unusual outbound traffic, such as encrypted communications to unknown IP addresses or suspicious domains.
6. Adversary accessing the C2 server with C2 client..
This is the final phase where the adversary uses the C2 server to send commands, tasks etc. to the victim user. This could help you evaluate the organization's ability to detect and respond to adversarial actions post-compromise.
Last updated on 25 December 2024
Go back to Blog and Random Thoughts