Internal Red Team Operations Framework: Building your organization's Internal Red Team | 20 October 2020
DEFINITIONS? WE STILL NEED TO DO THIS.
Vulnerability assessment is not Red Teaming.
The below-given write-up is just a PoC, which does not include the actual actions carried out as the part of the engagement.
Penetration testing is also not Red Teaming.
The below-given write-up is just a PoC, which does not include the actual actions carried out as the part of the engagement.
What is red team?
A RED TEAM IS A GROUP OF HIGHLY SKILLED PEOPLE THAT CONTINUOUSLY CHALLENGE THE PLANS, DEFENSIVE MEASURES AND SECURITY CONCEPTS. [Redteams.net]
BUILDING AN INTERNAL RED TEAM. [ADVERSARY SIMULATION and FULL SCOPE]
5 Phases of Internal Red Team Operations Framework [IRTO-F]
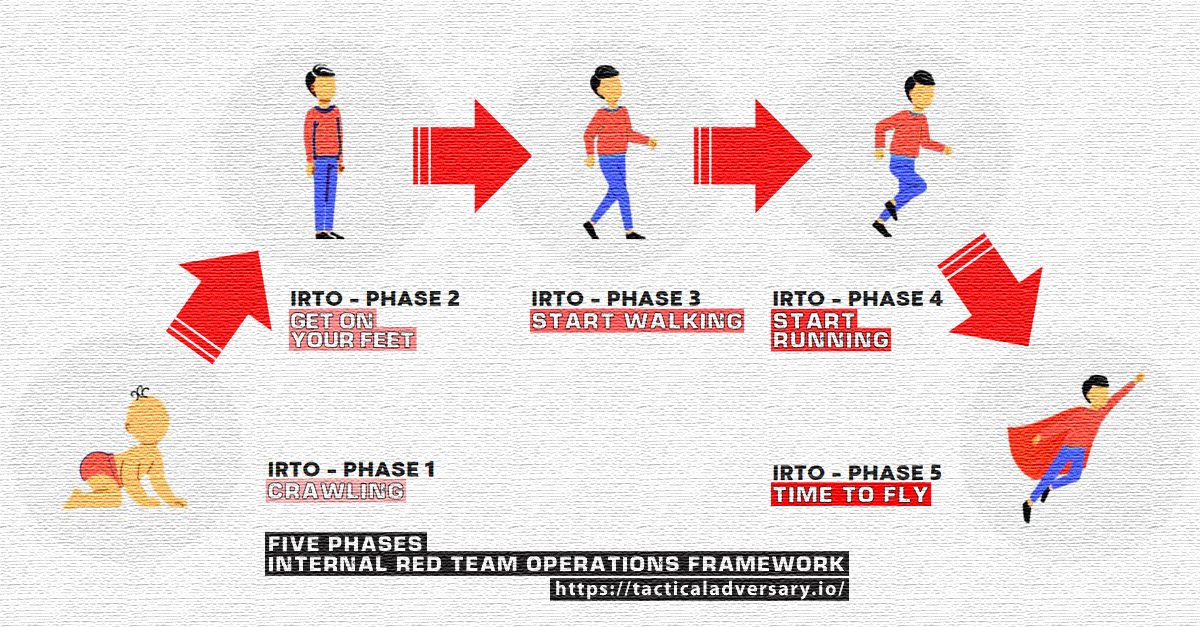
IRTO Phase 1: Crawling.
• Define the practical goals, objectives
• Get the budget approval
• Identify the crown jewels and people
• Rules of engagement (ROE), reporting and other process documentation
• Assistance from the Management and Legal department
• Understand the technologies in use – On premise infra, Cloud, Active Directory, Devices etc
• Understand the security posture of the organization
• Hire the talent – The Red Team
IRTO Phase 2: Get on your feet.
• Red Team external infrastructure (Digital ocean, GCP, AWS)
• Corp. tools, Improvised open source tooling capabilities
• Identifying the business specific risks
• Be friends with your organization’s Blue Team
• Adversary Emulation (Atomic red team, Caldera etc)
• Validate current defense mechanisms with blue team (MITRE)
• Manual campaigns against the organization and employees
• External attack surface discovery and mapping
• Designing a remediation process to address issues
IRTO Phase 3: Start walking.
• Improved Tools, techniques and procedures (TTP’s) based on current security posture
• Identify and eradicate findings 1, 2 - crown jewels and people*
• Evaluation of Incident response process*
• Automated Adversary Emulation
• Automated campaigns
• Targeted APT emulation based on Threat Intel
• Improvised RTO process documentation
IRTO Phase 4: Start running.
• Collaborative and continuous Purple team exercises
• Enterprise tooling capabilities
• Targeted campaigns against the Crown jewels and key people
• Overt physical security assessments
• Continuous awareness programme for employees and key people
• Continuous training process for operators and defenders
• Proactive remediation process and plans
IRTO Phase 5: Time to fly.
• Matured red team operations
• Significant improvement of organizational security posture
• Highly skilled operators
• Well defined Purple team model to measure the progress of Red and Blue team capabilities.
• Covert physical security assessments
• Custom tooling capabilities
• Continuous Adversary simulation to keep the defenders on their toes.
• Continuous RTO with well defined process
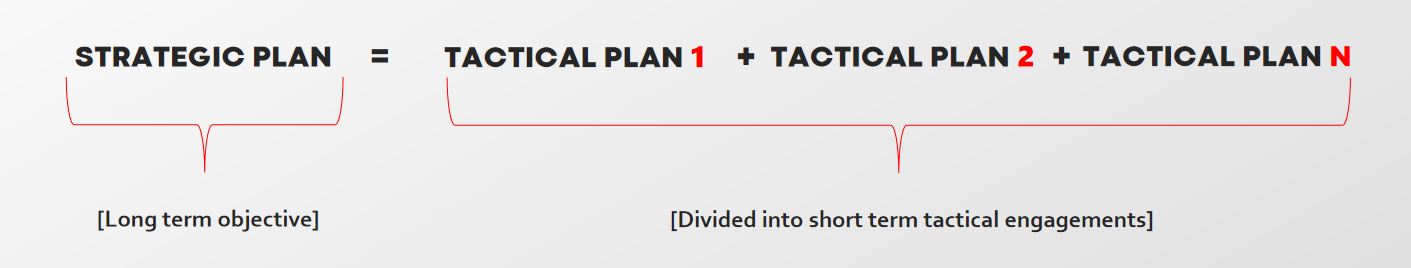
Planning: Strategic and tactical.
Originally presented at the DEF CON GROUPS (DCG) VR Village at DEFCON 28 Safemode conference on 7th Aug, 2020. BSides Delhi virtual conference on October 18, 2020.
Go back to Blog and Random Thoughts